TLS-SSL-Protocols: Difference between revisions
(Initial page) |
No edit summary |
||
| Line 1: | Line 1: | ||
As a way to mitigate the [https://www.openssl.org/~bodo/ssl-poodle.pdf Padding Oracle on Legacy Encryption (POODLE) attack], information technology (IT) administrators can disable all protocols older than TLSv1 via ActiveDirectory group policies. This page describes how to do this. | As a way to mitigate the [https://www.openssl.org/~bodo/ssl-poodle.pdf Padding Oracle on Legacy Encryption (POODLE) attack], information technology (IT) administrators can disable all protocols older than TLSv1 via ActiveDirectory group policies. This page describes how to do this. | ||
Using the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible | Using the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible policy template] with the group policy editor allows IT administrators to deploy computer-level policies that disable legacy protocols within Windows Schannel and deploy user-level policies that disable legacy protocols within Internet Explorer. Note that a computer-level disable policy for a protocol overrides Internet Explorer's configuration for that protocol. | ||
This template implements [https://technet.microsoft.com/en-us/library/security/3009008.aspx#sectionToggle3 Microsoft's recommended registry settings to disable SSLv3]. | |||
==Installation== | ==Installation== | ||
Save the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible | Save the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible policy template] as TLS-SSL-Protocols.adm within your Windows INF folder. This is typically <code>C:\Windows\INF</code>. | ||
==Include in a Policy== | ==Include in a Policy== | ||
This | This policy template includes two group policy targets: Computer and User. | ||
===Computer Policies=== | ===Computer Policies=== | ||
| Line 13: | Line 15: | ||
Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies. | Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies. | ||
To get started, either create a new group policy or edit an existing group policy that applies to groups of computers. The computer policy won't have an effect if it applies only to users and not to computers. | |||
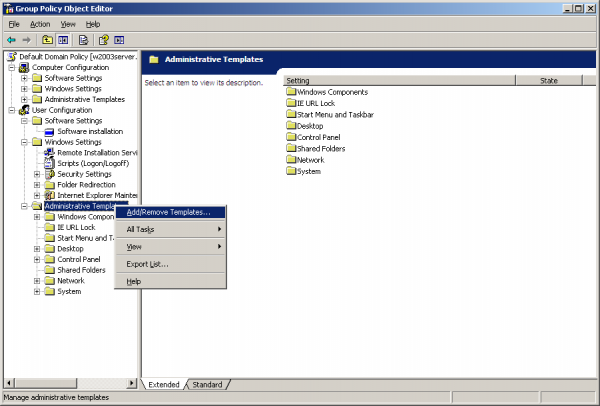
Right-click on the Computer Configuration | Administrative Templates folder. Alternatively, right-clicking on the User Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item. | |||
[[File:AddTemplate1.png|600px]] | |||
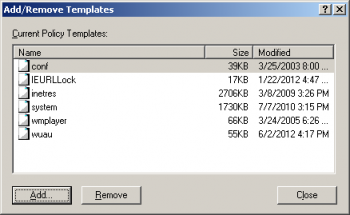
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed. | |||
[[File:AddTemplate2.png|350px]] | |||
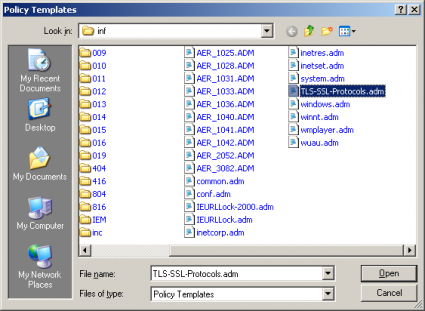
Select the TLS-SSL-Protocols.adm file and click the Open button. | |||
[[File:AddTemplate3.png|425px]] | |||
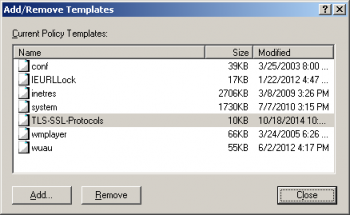
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue. | |||
[[File:AddTemplate4.png|350px]] | |||
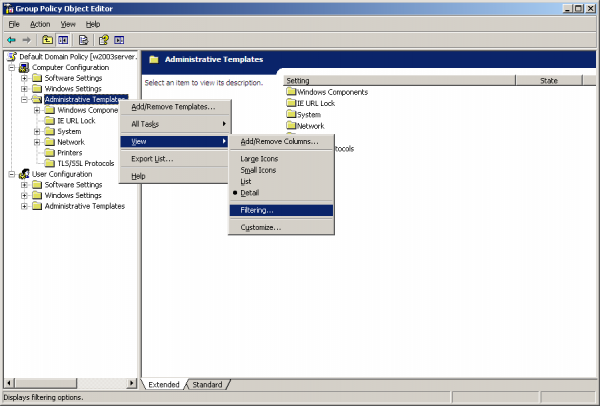
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the Computer Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item. | |||
[[File:Filtering-Computer.png|600px]] | |||
Revision as of 16:52, 18 October 2014
As a way to mitigate the Padding Oracle on Legacy Encryption (POODLE) attack, information technology (IT) administrators can disable all protocols older than TLSv1 via ActiveDirectory group policies. This page describes how to do this.
Using the Windows Server 2003 compatible policy template with the group policy editor allows IT administrators to deploy computer-level policies that disable legacy protocols within Windows Schannel and deploy user-level policies that disable legacy protocols within Internet Explorer. Note that a computer-level disable policy for a protocol overrides Internet Explorer's configuration for that protocol.
This template implements Microsoft's recommended registry settings to disable SSLv3.
Installation
Save the Windows Server 2003 compatible policy template as TLS-SSL-Protocols.adm within your Windows INF folder. This is typically C:\Windows\INF.
Include in a Policy
This policy template includes two group policy targets: Computer and User.
Computer Policies
The Computer policies configure the Windows Schannel protocol support, which impacts client software and server software with dedicated settings for each. Internet Explorer, email software, and any program that connects to the local network or Internet and uses Windows Schannel for securing its connections are affected by the client policies. Internet Information Server, .NET server software, and any program that listens for and accepts secure connections from the local network or Internet and uses Windows Schannel for securing connections are affected by the server policies.
Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies.
To get started, either create a new group policy or edit an existing group policy that applies to groups of computers. The computer policy won't have an effect if it applies only to users and not to computers.
Right-click on the Computer Configuration | Administrative Templates folder. Alternatively, right-clicking on the User Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item.
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed.
Select the TLS-SSL-Protocols.adm file and click the Open button.
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue.
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the Computer Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item.